Traditional networks have a natural immunity to common attacks due to the nature of their closed hardware, stable design, software homogeneity, and decentralized control. For example; If an attacker exploits a vulnerability for devices made by a company, the network will be affected only in the part that contains devices belonging to this company, and the rest of the devices will not be affected because they belong to other manufacturers that may not contain the same vulnerability.
In SDN networks, the existence of a shared open flow protocol between devices belonging to different companies will increase the risk of threats and lead to widespread crashes. Therefore, even though SDN is a great technology in the network world; But it somehow increased the threats; Therefore, it is imperative to discuss security and reliability issues and solutions that should be taken into consideration when designing an SDN (1, 2).
Threats and threats to SDN networks
SDN networks have two main characteristics that make them attractive to attackers and hackers, and a source of concern for the owners of these networks, and they are:
1- The network is programmed using software.
2- Centralization of network control, and then access to one of the controllers means access and control of the entire network.
Below we list the most important threats that may face us in SDN networks, which we group in Figure (1), with simple solutions suggested (2).
1- Injecting false or false information:
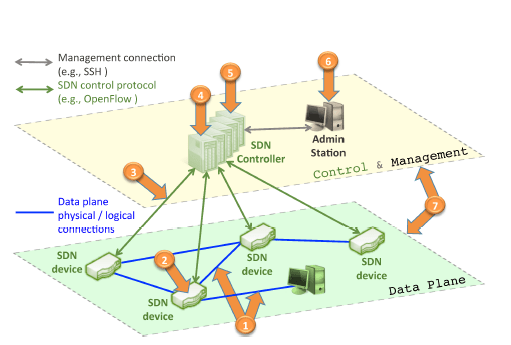
Switches or routers can be attacked by the presence of tampered devices in the network, or by a malicious attacker using any component of the network (router, switch, server, etc.); This is to launch parcels in large numbers in order to achieve a Denial of Service (DOS *) attack, which may be – for example – against switches that use the Open Flow protocol, as all the memories within the switch are consumed.
proposed solution:
The use of Intrusion Detection System (IDS), supported by Runtime Root-Cause Analysis, to detect the abnormal behavior of network elements, in addition to the use of mechanisms for dynamic control of the behavior of the switch, such as setting a certain limit on the rate of control requests.
2- Attacking the vulnerabilities of the switches:
Attacking or controlling a single switch means the possibility of ignoring a parcel, redirecting a parcel to the wrong destination, copying certain parcels, slowing the parcel’s flow within the network, or even injecting data or fake requests into the network, in order to stop the work of the controllers or switches. Neighboring.
proposed solution:
Use of mechanisms to conduct software validations; Such as self-confidence management systems for software components, or the use of mechanisms to monitor and detect abnormal behavior of network devices (2).
3- Attacking Control Layer Communications:
May be used to conduct a DoS attack or steal data. Even if the connections are encrypted; But the lines of the control layer remain threatened; Communications security is measured by the strength of its weakest lines or elements, and this weakness may be due to self-signed certificates, digital certificates granted by an insecure party, or because of weak applications and libraries. This opens up the so-called Man-in-the-Middle (MITM)** attack. If an attacker succeeds in gaining control of control layer communications, he can accumulate enough force that varies according to the number of switches coming under his control, and then launch a Denial of Service (DOS) attack.
proposed solution:
Securing communication between controllers by encoding this layer, in addition to the possibility of using dynamic and secure mechanisms to link devices to ensure trust between control layer devices and data layer devices (2).
4- Attacking controller weaknesses:
This attack is considered one of the most dangerous threats to SDN networks; Malfunctioning a single console or infecting it with a malicious attack can bring down the entire network. Also, the use of the Intrusion Detection System (IDS) may not be sufficient; Because it is difficult to find the exact assembly of events that may lead to the generation of a certain behavior, and the most important thing is to know that this behavior is malicious behavior.
proposed solution:
Several technologies can be used, such as repetition or replication (to detect, eliminate, or mask abnormal behavior). It is also important to secure all sensitive elements within the controller (such as the encryption keys). In addition to that; The use of security policies can ensure the correct implementation of the behavior of these technologies, as well as the interfaces that can be used by applications and the rules and commands that these applications can generate to program the network can be restricted (2).
5- Lack of mechanisms to ensure trust between controllers and management applications:
Similar to Threat # 3; Controllers and apps lack the ability to establish trusted relationships.
The main difference from the indicated threat is the manner in which the testimony is constructed. The technologies used to authenticate network devices differ from those used for applications.
proposed solution:
Use self-confidence management mechanisms to ensure applications are trusted throughout their life cycle (2).
6- Attacking the weak points of management stations:
Management stations are usually located within traditional networks; But it is also used in SDNs to access the network controller. The difference is that if only one management device or station is compromised; Then this risk will increase dramatically in SDNs, because it will be easy to reprogram the network from one location.
proposed solution:
Use of protocols that require double verification; For example, a request to access a controller requires a two-person mandate. Foolproof recovery mechanisms can also be used to ensure a reliable state after restart (2).
7- Lack of reliable sources for characterization and recovery:
Having reliable sources for characterization and recovery allows an understanding of the cause of the problem detected and treatment of a quick return to safe mode. In order to investigate and verify an incident, we need reliable information from all parts and areas that make up the network, as well as that; This information will only be useful if reliability is guaranteed. In addition, recovery requires secure and reliable system monitoring to ensure the fast and correct recovery of network elements to the state in which they were operating.
proposed solution:
The use of recording and tracking mechanisms, they are needed at the data and control levels, knowing that in order to be effective, they must not be erased or immutable. Records should also be stored in remote and secure environments (2).
*Denial of Service : A denial of service attack – or what is called a Distributed Denial of Service – is used to make a service on the Internet unresponsive, down completely, or respond in a different way that can be exploited to collect information, for example. The attack occurs by making repeated requests to the server until its resources are depleted. In the case of a distributed environment, orders are served by multiple clients at the same time; This significantly increases the load on the target (3).
*Man In Middle : A method of gaining access to the system is by attempting to impersonate a server component rather than a customer, often referred to as a “man-in-the-middle attack”. In this process, the attacker gains access to confidential information within the messages; Such as customer credentials (4).
Sources:
1- Deb R,Roy S,. Dynamic vulnerability assessments of software-defined networks. Innovations Syst Softw Eng [Internet]. 2020 [cited 30 April 2021];16, 45–51. Available from: Here
2- Kreutz D,Ramos F, Verissimo p: Towards secure and dependable software-defined networks. Proceedings of the second ACM SIGCOMM workshop on Hot topics in software defined networking.Hong Kong: ACM; [Internet] 2013[cited 29 April 2021]. p.55–60. Available from: Here
3- Lau F, Rubin S, M. Smith M and Trajkovic L: Distributed denial of service attacks. Smc 2000 conference proceedings. 2000 ieee international conference on systems, man and cybernetics. ‘cybernetics evolving to systems, humans, organizations, and their complex interactions’. Nashville, TN, USA : IEEE; [Internet] 2000[cited 10 May 2021]. p.2275-2280. Available from: Here
4- Conti M, Dragoni N, Foh C, Lesyk V, A Survey of Man In The Middle Attacks. Communications Surveys & Tutorials IEEE [Internet]. 2016[cited 10 May 2021];18(3): 2027-2051. Available from: Here


0 Comments